Caddy with custom path
Caddy is a powerful and flexible web server that can be used to secure your Remnawave panel.
Installation
First of all, create a directory for Caddy.
mkdir -p /opt/remnawave/caddy && cd /opt/remnawave/caddy
Then create a docker-compose.yml file.
touch docker-compose.yml && nano docker-compose.yml
And add the following content to the file:
services:
remnawave-caddy:
image: remnawave/caddy-with-auth:latest
container_name: 'remnawave-caddy'
hostname: remnawave-caddy
restart: always
environment:
- AUTH_TOKEN_LIFETIME=3600
- REMNAWAVE_PANEL_DOMAIN=PANEL_DOMAIN
- REMNAWAVE_CUSTOM_LOGIN_ROUTE=supersecretroute
- AUTHP_ADMIN_USER=LOGIN_USERNAME
- AUTHP_ADMIN_EMAIL=LOGIN_EMAIL
- AUTHP_ADMIN_SECRET=LOGIN_PASSWORD
ports:
- '0.0.0.0:443:443'
networks:
- remnawave-network
volumes:
- ./Caddyfile:/etc/caddy/Caddyfile
- remnawave-caddy-ssl-data:/data
networks:
remnawave-network:
name: remnawave-network
driver: bridge
external: true
volumes:
remnawave-caddy-ssl-data:
driver: local
external: false
name: remnawave-caddy-ssl-data
Configuring .env variables
You need to set a domain name for your Remnawave panel. Caddy will automatically issue a certificate for it.
REMNAWAVE_PANEL_DOMAIN=panel.domain.com
Custom login route. This path will be used ONLY for the login page. There will be no redirect if you open the dashboard without being previously authenticated. Only people who know this path will be able to access the panel.
REMNAWAVE_CUSTOM_LOGIN_ROUTE=supersecretroute
Admin credentials. Make sure to use a strong password.
AUTHP_ADMIN_USER=admin
AUTHP_ADMIN_EMAIL=admin@domain.com
AUTHP_ADMIN_SECRET=strong_password
Token lifetime.
AUTH_TOKEN_LIFETIME=3600
Caddyfile
Lets deep dive into the Caddyfile.
First of all, you need to select one of our predefined setups.
We recommend using full security setup with MFA for production environments where you will be issuing API-keys.
You will able to login only via this path (REMNAWAVE_CUSTOM_LOGIN_ROUTE).
Full security setup with MFA
- All routes are protected by authentication. (Frontend, Backend)
- All API-endpoints are protected, includes /api/sub/* endpoints.
- Login requires MFA with OTP-codes.
- Special API-keys can be issued for /api/* endpoints.
- Full domain protection.
Run the command below to download the Caddyfile.
curl -o Caddyfile https://raw.githubusercontent.com/remnawave/caddy-with-auth/refs/heads/main/examples/custom-webpath-with-auth-and-protected-api-route/Caddyfile
API routes without auth (api/*)
- Routes are protected by authentication. (Frontend)
- Login requires MFA with OTP-codes. (Frontend)
- All API-endpoints are not protected! (/api/* is public)
This setup exposes the /api/* endpoints to the public internet.
All endpoints will not require authentication, but will still use the Remnawave security features.
We recommend using full security setup with MFA for production environments where you will be issuing API-keys.
Run the command below to download the Caddyfile.
curl -o Caddyfile https://raw.githubusercontent.com/remnawave/caddy-with-auth/refs/heads/main/examples/custom-webpath-with-auth-with-api-without-auth/Caddyfile
/api/sub/* endpoints without auth
- Routes are protected by authentication. (Frontend)
- Login requires MFA with OTP-codes. (Frontend)
- Only
/api/sub/*endpoints is public, other endpoints are protected.
This setup exposes the /api/sub/* endpoints to the public internet.
We recommend using full security setup with MFA for production environments where you will be issuing API-keys and use @remnawave/subscription-page for public subscription page.
Run the command below to download the Caddyfile.
curl -o Caddyfile https://raw.githubusercontent.com/remnawave/caddy-with-auth/refs/heads/main/examples/custom-webpath-with-auth-with-opened-api-sub/Caddyfile
Running the container
After you have selected one of the setups above, you can start the container with the following command.
docker compose up -d && docker compose logs -f
Accessing the panel
After the container is running, you can access the panel at https://panel.domain.com/REMNAWAVE_CUSTOM_LOGIN_ROUTE.
On the first start, you will be prompted to add a MFA method.
We recommend using Google Authenticator.
Disable MFA
If you want to completely disable MFA, you can do this by editing the Caddyfile.
Open the Caddyfile and change the following line:
cd /opt/remnawave/caddy && nano Caddyfile
Find the following lines, and remove the require mfa line.
transform user {
match origin local
action add role authp/admin
require mfa
}
After that, you can restart the container with the following command.
docker compose down && docker compose up -d && docker compose logs -f
Accessing Auth Portal page
You can access the Auth Portal page at https://<your-domain>/REMNAWAVE_CUSTOM_LOGIN_ROUTE/auth.
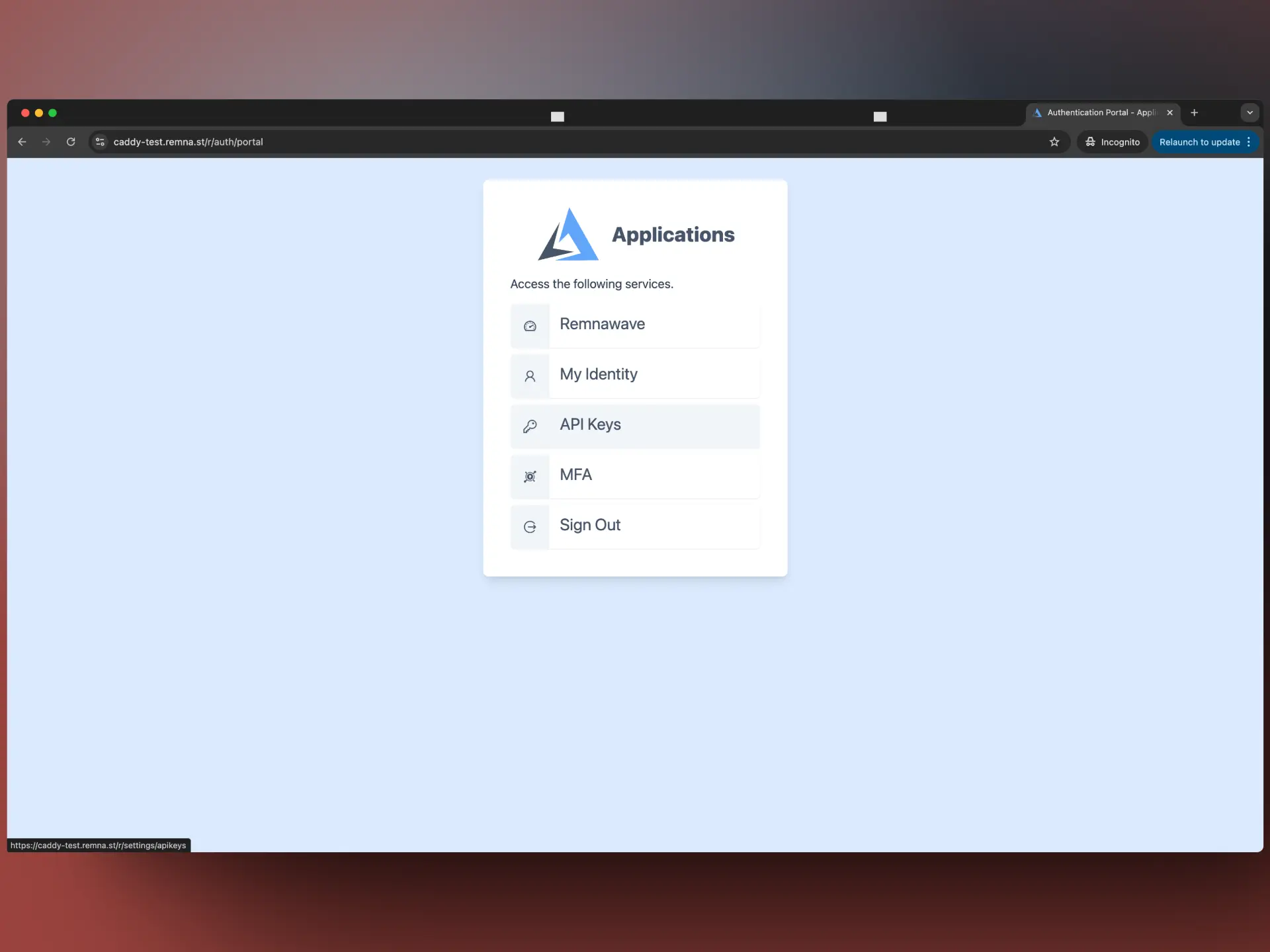
Here you can quickly go to the Remnawave dashboard or manage some of Auth Portal settings.
In the MFA section, you can delete or add new MFA methods.
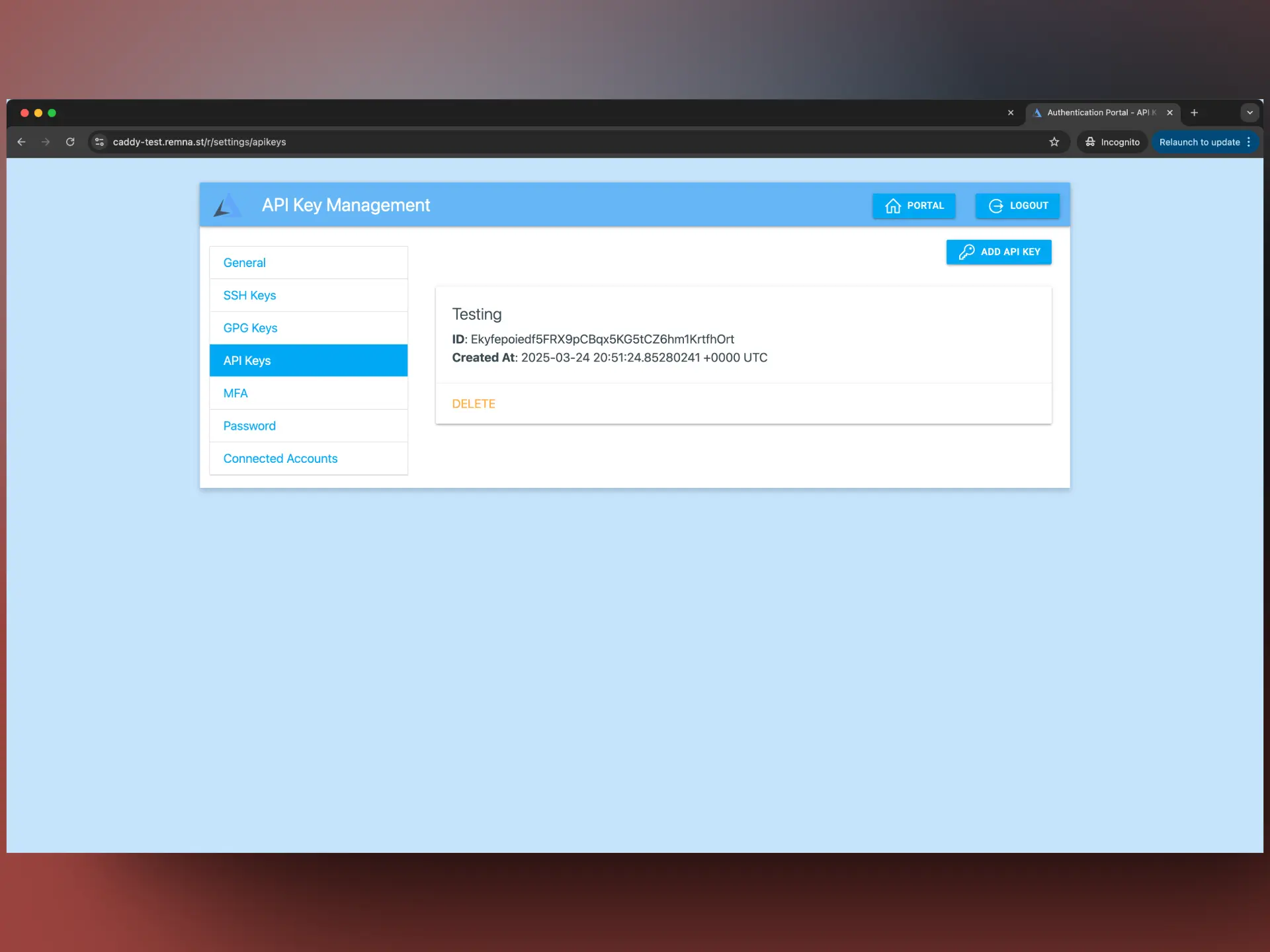
Issuing API-keys
You can access the Auth Portal page at https://<your-domain>/REMNAWAVE_CUSTOM_LOGIN_ROUTE/auth.
On the Auth Portal page, you can issue API-keys, click on the API-keys tab.
After you issue an API-key, you can use it in the X-Api-Key header of your requests to the API.
Example: X-Api-Key: YxOovHLnpkcmSig5082egcHnyTk8SK4dNGAFHgZ2LKZezgj5oUj2FA2IR2sMwbALnP9YNpzZ